All Categories
Featured
Table of Contents
Amazon currently typically asks interviewees to code in an online document data. Currently that you understand what questions to expect, allow's concentrate on exactly how to prepare.
Below is our four-step preparation strategy for Amazon information researcher prospects. Prior to investing tens of hours preparing for an interview at Amazon, you must take some time to make certain it's in fact the right firm for you.
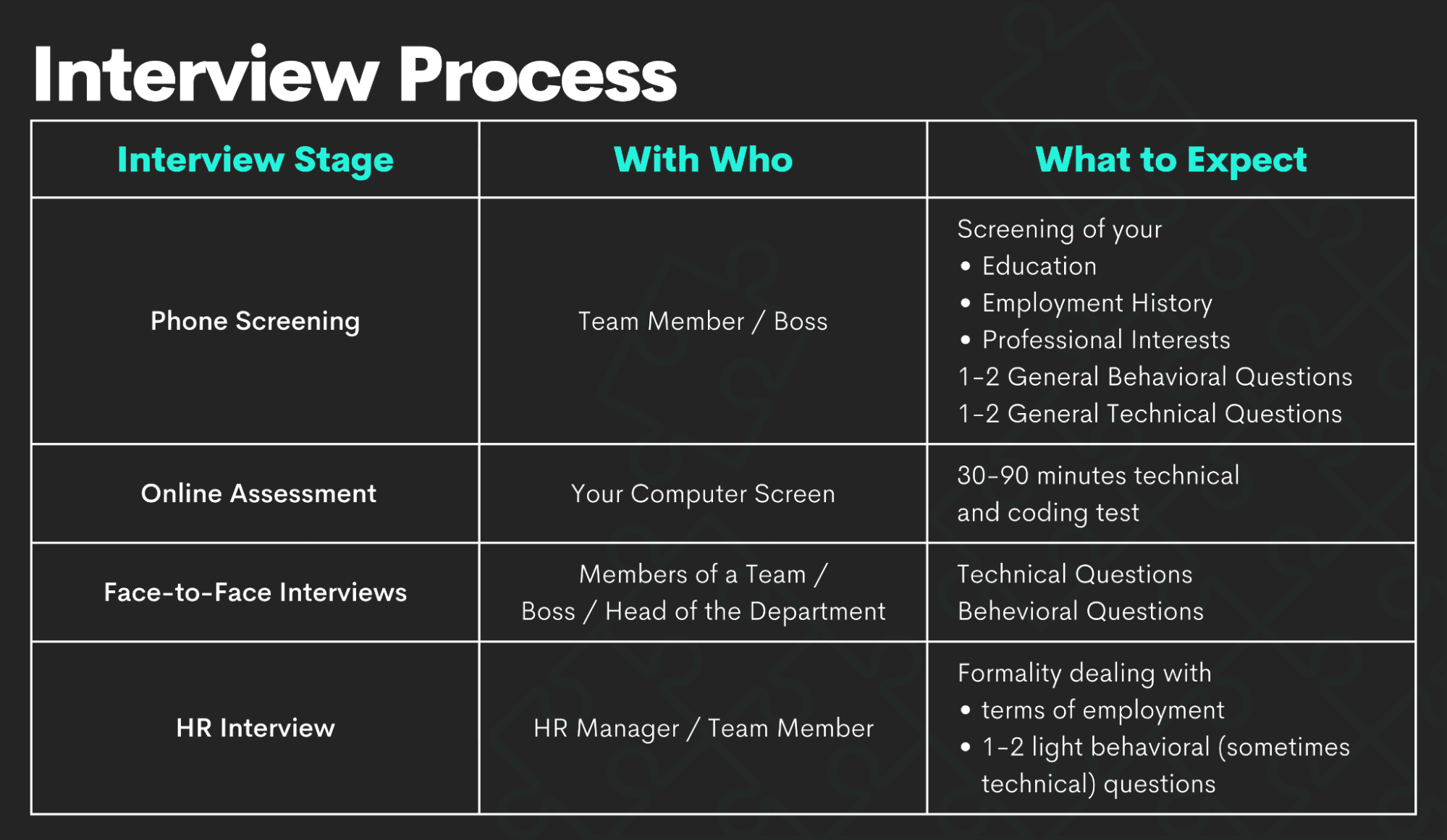
, which, although it's created around software program development, should give you a concept of what they're looking out for.
Note that in the onsite rounds you'll likely have to code on a white boards without being able to implement it, so practice creating through troubles on paper. Supplies totally free programs around initial and intermediate maker understanding, as well as information cleaning, information visualization, SQL, and others.
Critical Thinking In Data Science Interview Questions
Make certain you have at least one story or example for every of the concepts, from a wide variety of settings and tasks. Lastly, a fantastic method to exercise every one of these various kinds of concerns is to interview yourself aloud. This might sound unusual, but it will significantly boost the way you connect your solutions throughout an interview.

One of the primary obstacles of information scientist interviews at Amazon is interacting your different answers in a method that's simple to comprehend. As a result, we highly suggest exercising with a peer interviewing you.
They're unlikely to have insider expertise of interviews at your target firm. For these reasons, several prospects miss peer mock interviews and go right to mock meetings with a specialist.
Leveraging Algoexpert For Data Science Interviews
That's an ROI of 100x!.
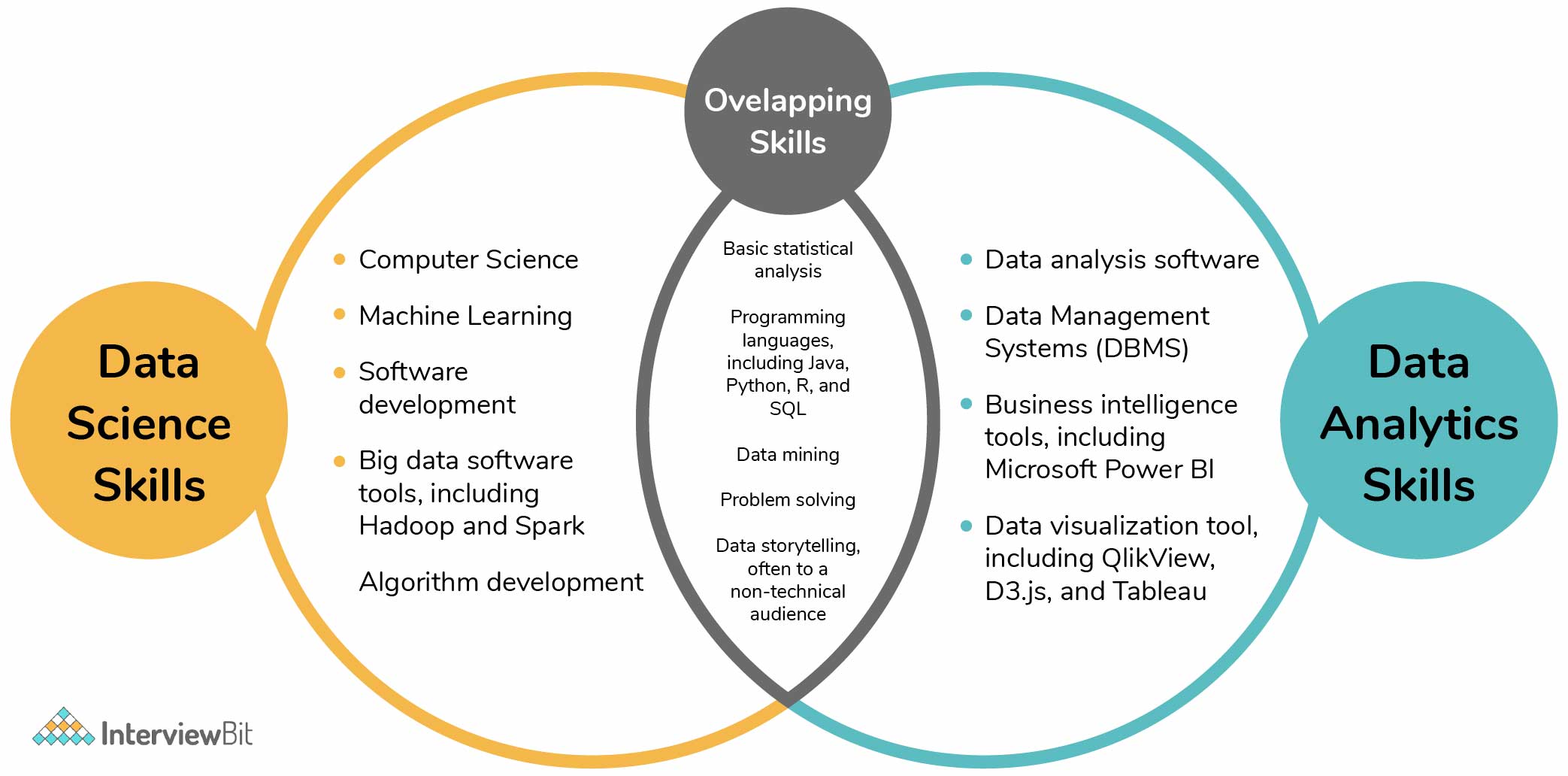
Traditionally, Information Science would certainly concentrate on mathematics, computer science and domain name knowledge. While I will briefly cover some computer system science principles, the bulk of this blog site will mainly cover the mathematical essentials one could either need to clean up on (or even take a whole program).
While I recognize a lot of you reading this are extra mathematics heavy by nature, recognize the mass of data scientific research (risk I claim 80%+) is collecting, cleansing and handling information into a helpful kind. Python and R are one of the most prominent ones in the Information Science space. Nevertheless, I have additionally encountered C/C++, Java and Scala.
Mock System Design For Advanced Data Science Interviews

It is common to see the majority of the data researchers being in one of two camps: Mathematicians and Data Source Architects. If you are the 2nd one, the blog site will not assist you much (YOU ARE ALREADY REMARKABLE!).
This might either be accumulating sensing unit data, parsing sites or accomplishing surveys. After collecting the information, it requires to be transformed into a usable kind (e.g. key-value store in JSON Lines files). When the data is accumulated and put in a usable style, it is vital to perform some data high quality checks.
Key Data Science Interview Questions For Faang
Nevertheless, in cases of fraud, it is extremely common to have heavy class discrepancy (e.g. just 2% of the dataset is real scams). Such information is essential to choose the ideal selections for function engineering, modelling and design evaluation. For even more information, check my blog on Fraud Discovery Under Extreme Class Imbalance.

In bivariate analysis, each feature is compared to various other features in the dataset. Scatter matrices permit us to locate concealed patterns such as- functions that should be engineered with each other- attributes that might require to be removed to prevent multicolinearityMulticollinearity is actually a problem for several versions like direct regression and for this reason needs to be taken treatment of appropriately.
In this area, we will certainly discover some usual function engineering techniques. Sometimes, the attribute by itself might not supply useful information. For example, picture making use of net use information. You will have YouTube users going as high as Giga Bytes while Facebook Carrier users utilize a pair of Mega Bytes.
Another issue is making use of categorical worths. While specific worths are common in the information science globe, realize computers can only understand numbers. In order for the specific worths to make mathematical feeling, it requires to be transformed right into something numerical. Usually for categorical values, it prevails to do a One Hot Encoding.
Interview Prep Coaching
Sometimes, having way too many sparse dimensions will certainly hamper the performance of the design. For such situations (as frequently done in photo acknowledgment), dimensionality decrease formulas are made use of. An algorithm typically utilized for dimensionality decrease is Principal Elements Analysis or PCA. Find out the technicians of PCA as it is also among those subjects among!!! To learn more, have a look at Michael Galarnyk's blog on PCA making use of Python.
The common classifications and their sub categories are clarified in this section. Filter techniques are normally utilized as a preprocessing action.
Usual techniques under this classification are Pearson's Correlation, Linear Discriminant Evaluation, ANOVA and Chi-Square. In wrapper methods, we attempt to make use of a subset of attributes and train a version using them. Based on the reasonings that we draw from the previous design, we determine to add or get rid of functions from your part.
Machine Learning Case Study
Common methods under this category are Forward Selection, In Reverse Removal and Recursive Feature Removal. LASSO and RIDGE are typical ones. The regularizations are offered in the equations below as reference: Lasso: Ridge: That being claimed, it is to comprehend the auto mechanics behind LASSO and RIDGE for meetings.
Supervised Understanding is when the tags are available. Without supervision Understanding is when the tags are not available. Obtain it? Manage the tags! Pun meant. That being said,!!! This mistake is enough for the interviewer to terminate the meeting. One more noob blunder people make is not stabilizing the functions before running the model.
Linear and Logistic Regression are the a lot of fundamental and generally utilized Device Discovering formulas out there. Before doing any kind of evaluation One usual meeting blooper individuals make is starting their analysis with a more complex version like Neural Network. Benchmarks are essential.
Latest Posts
How To Negotiate Your Software Engineer Salary Like A Pro
Microsoft Software Engineer Interview Preparation – Key Strategies
Software Engineering Interview Tips From Hiring Managers